BPS: ‘Frauds Resulted In Loss Of $1.3M & $4M’
[Updated] Police have received three reports in the last 10 days from local businesses “regarding significant cyber-enabled fraud incidents,” and “two frauds resulted in the loss of $1.3M and $4M in separate incidents, and the third attempt at a different business was discovered before funds were actually transferred.”
“An email impersonating the executive is sent to the accounts department employee, which requests an urgent overseas payment to be made,” the police explained, adding that they urge ”all companies to review their business processes to guard against this type of cyber-crime.”
The police said, “The Bermuda Police Service [BPS] wishes to advise the Bermuda business community in regards to an emerging cyber threat named ‘Business Email Compromise’ [BEC], also called ‘CEO fraud’, which has so far resulted in the loss or attempted loss of significant sums from local businesses.
“Organised Crime Groups make use of publicly available contact information to collect email data of company executives and accounts department employees.
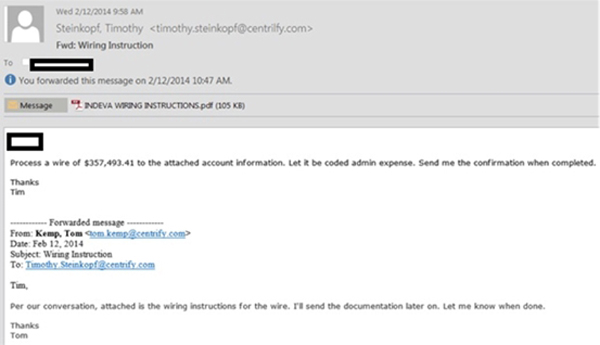
“An email impersonating the executive is sent to the accounts department employee, which requests an urgent overseas payment to be made. An example of a spoofed email is attached. The below example relates to a generic email taken from the internet.
“In 2016, the FBI issued a press release confirming this type of fraud had seen a 1300% increase, with a combined loss of over $3 billion.
“The FBI note the characteristics of Business Email Compromise include:
- Businesses and associated personnel using open source e-mail accounts are predominantly targeted.
- Individuals responsible for handling wire transfers within a specific business are targeted.
- Spoofed e-mails very closely mimic a legitimate e-mail request.
- Hacked e-mails often occur with a personal e-mail account.
- Fraudulent e-mail requests for a wire transfer are well-worded, specific to the business being victimized, and do not raise suspicions to the legitimacy of the request.
- The phrases “code to admin expenses” or “urgent wire transfer” were reported by victims in some of the fraudulent e-mail requests.
- The amount of the fraudulent wire transfer request is business-specific; therefore, dollar amounts requested are similar to normal business transaction amounts so as not to raise doubt.
- Fraudulent e-mails received have coincided with business travel dates for executives whose e-mails were spoofed.
- Victims report that IP addresses frequently trace back to free domain registrars.
Detective Superintendent Sean Field-Lament of the BPS Crime Division states, “I wish to raise awareness of the Bermuda business community in regards to an emerging cyber threat named ‘Business Email Compromise’ [BEC], also called ‘CEO fraud’.
“The Organized and Economic Crime Department has received three reports in the last 10 days from local businesses regarding significant cyber-enabled fraud incidents.
“Two frauds resulted in the loss of $1.3M and $4M in separate incidents, and the third attempt at a different business was discovered before funds were actually transferred. The BPS would encourage all companies to review their business processes to guard against this type of cyber-crime.”
“Prevention and awareness are the key suggestions for protection and best practice:
- Businesses with an increased awareness and understanding of the BEC scam are more likely to recognize when they have been targeted by BEC fraudsters, and are therefore more likely to avoid falling victim and sending fraudulent payments.
- Businesses that deploy robust internal prevention techniques at all levels [especially targeting front line employees who may be the recipients of initial phishing attempts], have proven highly successful in recognizing and deflecting BEC attempts.
- Some financial institutions reported holding their customer requests for international wire transfers for an additional period of time, to verify the legitimacy of the request.
“Further to the above, the FBI has compiled a list of self-protection strategies:
- Avoid free web-based e-mail accounts: Establish a company domain name and use it to establish company e-mail accounts in lieu of free, web-based accounts.
- Be careful what is posted to social media and company websites, especially job duties/descriptions, hierarchal information, and out of office details.
- Be suspicious of requests for secrecy or pressure to take action quickly.
- Consider additional IT and financial security procedures, including the implementation of a 2-step verification process.
For example
- Out of Band Communication: Establish other communication channels, such as telephone calls, to verify significant transactions. Arrange this second-factor authentication early in the relationship and outside the e-mail environment to avoid interception by a hacker.
- Digital Signatures: Both entities on each side of a transaction should utilize digital signatures. This will not work with web-based e-mail accounts. Additionally, some countries ban or limit the use of encryption.
- Delete Spam: Immediately report and delete unsolicited e-mail [spam] from unknown parties. DO NOT open spam e-mail, click on links in the e-mail, or open attachments. These often contain malware that will give subjects access to your computer system.
- Forward vs. Reply: Do not use the “Reply” option to respond to any business e-mails. Instead, use the “Forward” option and either type in the correct e-mail address or select it from the e-mail address book to ensure the intended recipient’s correct e-mail address is used.
- Consider implementing Two Factor Authentication [TFA] for corporate e-mail accounts. TFA mitigates the threat of a subject gaining access to an employee’s e-mail account through a compromised password by requiring two pieces of information to login: something you know [a password] and something you have [such as a dynamic PIN or code].
- Significant Changes: Beware of sudden changes in business practices. For example, if a current business contact suddenly asks to be contacted via their personal e-mail address when all previous official correspondence has been through company e-mail, the request could be fraudulent. Always verify via other channels that you are still communicating with your legitimate business partner.
- Create intrusion detection system rules that flag e-mails with extensions that are similar to company e-mail. For example, legitimate e-mail of abc_company.com would flag fraudulent e-mail of abc-company.com.
- Register all company domains that are slightly different than the actual company domain.
- Verify changes in vendor payment location by adding additional two-factor authentication such as having a secondary sign-off by company personnel.
- Confirm requests for transfers of funds. When using phone verification as part of the two-factor authentication, use previously known numbers, not the numbers provided in the e-mail request.
- Know the habits of your customers, including the details of, reasons behind, and amount of payments.
- Carefully scrutinize all e-mail requests for transfers of funds to determine if the requests are out of the ordinary.
“Additional information is publicly available on the United States Department of Justice website at under the ‘Topical White Papers’ publication entitled “Best Practices for Victim Response and Reporting of Cyber Incidents.”
Update 3.04pm: Detective Superintendent Sean Field-Lament of the Bermuda Police Service [BPS] Crime Division said, “I wish to continue to raise awareness of the Bermuda business community in regards to an emerging cyber threat named ‘Business Email Compromise’ [BEC], also called ‘CEO fraud’.
“The Organized and Economic Crime Department [OECD] has now received four reports in the last 2 weeks from local businesses regarding significant cyber-enabled fraud incidents.
“Two frauds resulted in the loss of $1.3M [million] and $4M [million] in separate incidents, and the other two attempts at different businesses were discovered before funds were actually transferred.
“The BPS would encourage all companies to robustly review their business processes to guard against this type of cyber-crime.
“The scam is a well-known fraud and is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
“It targets businesses that work with foreign suppliers and/or regularly perform wire transfer payments.
“It has resulted in numerous businesses attacked worldwide, including in all 50 U.S. states and in over 100 countries.
“It appears that scammers are making attempts at local businesses but there is no suggestion that Bermuda is being targeted generally.
“Bermuda is not immune to BEC scams. We have had several variations of the fraud reported in the last few years, and we are working with the FBI on the latest incidents.”
Read More About
Category: All, Business, Crime, News, technology



Come on! Really? Someone responsible for millions of dollars of a companies money did not verify an email request to transfer those monies outside of the company? They should have never been put in that position of responsibility in the first place if they did!
It’s not that simple, these emails look exactly like they have come from a verifiable source, e.g. your boss. They even sign off using initials or shortened forms that your boss uses because they’ve been in your email system and seen how the process works. It slips through the net like any other request that particular day.
I hope they had a cyber insurance policy to cover these losses!!
Actually it is that simple. Any business with $4 million + in cash in their accounts should have a system of authorizations setup. The Bank who held these funds would also need to ensure those authorizations were verified before acting on the business’ instructions to transfer any money. It happens at the consumer level with credit card charges why wouldn’t it happen at the corporate level? Its a basic financial control. Someone dropped the ball!
On the topic of fraud, what happened to all of Cain and Burt’s ICO talking? I guess it doesn’t sound as good now that the main cryptos have all tanked. ICOs would bring a whole lot of fraud to Bermuda since most are scams. BPS needs to push to keep them off the island so they don’t get buried in the work load they would bring.
You are highly misinformed. Most ICOs are not scams, its the pump and dump build up hype is what catches inexperienced traders out. The ‘main cryptos’ have consolidated from their previous astronomical highs which is expected in any market. Stop feeding into the fear propaganda machine from the banks.
Make me wonder if these money scams could be inside jobs.
It is not nessesarly the little guy.
Where are the “Whistle Blowers” ?
Madoff talkes first prize for the oldest trick in the book and they did not see it coming.
Many businesses suffer from their own trying to take advantage of their employer,caused by lack of supervision and acountability, two thirds of the product shortages are usualy internal, from two hour lunch breaks and much more. ” As Stealing Time ” is one of the all time favorites.
Who pays for all of this ? YOU DO !